Cyberattacks are an escalating threat to modern businesses, with global damage estimated at $10.5 trillion by 2025. This figure only reflects monetary loss; many breaches also inflict reputational damage. Despite ongoing efforts to adapt and strengthen security posture, traditional perimeter-based security is increasingly ineffective against sophisticated threats. Once breached, these models leave internal systems vulnerable to lateral movement and deeper compromise. This is why businesses are shifting to a zero trust security model, built on the premise that attacks may originate from both external and internal sources within the network.
In contrast to traditional security methods that follow a reliable internal network and an untrusted external network, the zero trust network model operates on a simpler but powerful principle: “trust no one, verify everyone.” Zero trust is emerging as one of the growing trends for modern app security resilience today. It offers them a more innovative, layered approach to protecting critical business data and systems. So, how do you move from implied trust to Zero Trust? In this blog, we will explore how zero trust helps you identify who is at risk and the common pathways attackers exploit. More importantly, we will discuss how to implement zero trust and the challenges organizations face when adopting a zero trust network model.
What is Zero Trust?
Zero trust is a security strategy that, instead of focusing on the network perimeter, enforces security measures for each connection between users, systems, applications, and data. So, when businesses start with how to implement a zero trust security model, they can stay protected against cybersecurity risks posed by remote workers, hybrid cloud services, personally owned devices, and other components of today’s corporate networks.
Key Zero Trust Components
- Verify explicitly: Authenticate and authorize every user and device.
- Use least privilege: Grant minimum required access.
- Assume breach: Design systems as if attackers are already inside.
Benefits of Zero Trust Implementation
- It strengthens the overall security posture by limiting lateral movement once a breach occurs.
- Reduces breach impact through strict segmentation and least-privilege access.
- Protects remote and hybrid environments by eliminating implicit trust across devices and users.
- Improves threat detection with continuous monitoring and adaptive authentication.
- Aligns with compliance mandates by enforcing granular access controls and auditability.
How to Implement Zero Trust Security: A Step-by-Step Guide
These steps will help you in your zero trust implementation journey to strengthen security, limit vulnerabilities, and ensure only authorized personnel and devices can access sensitive resources.
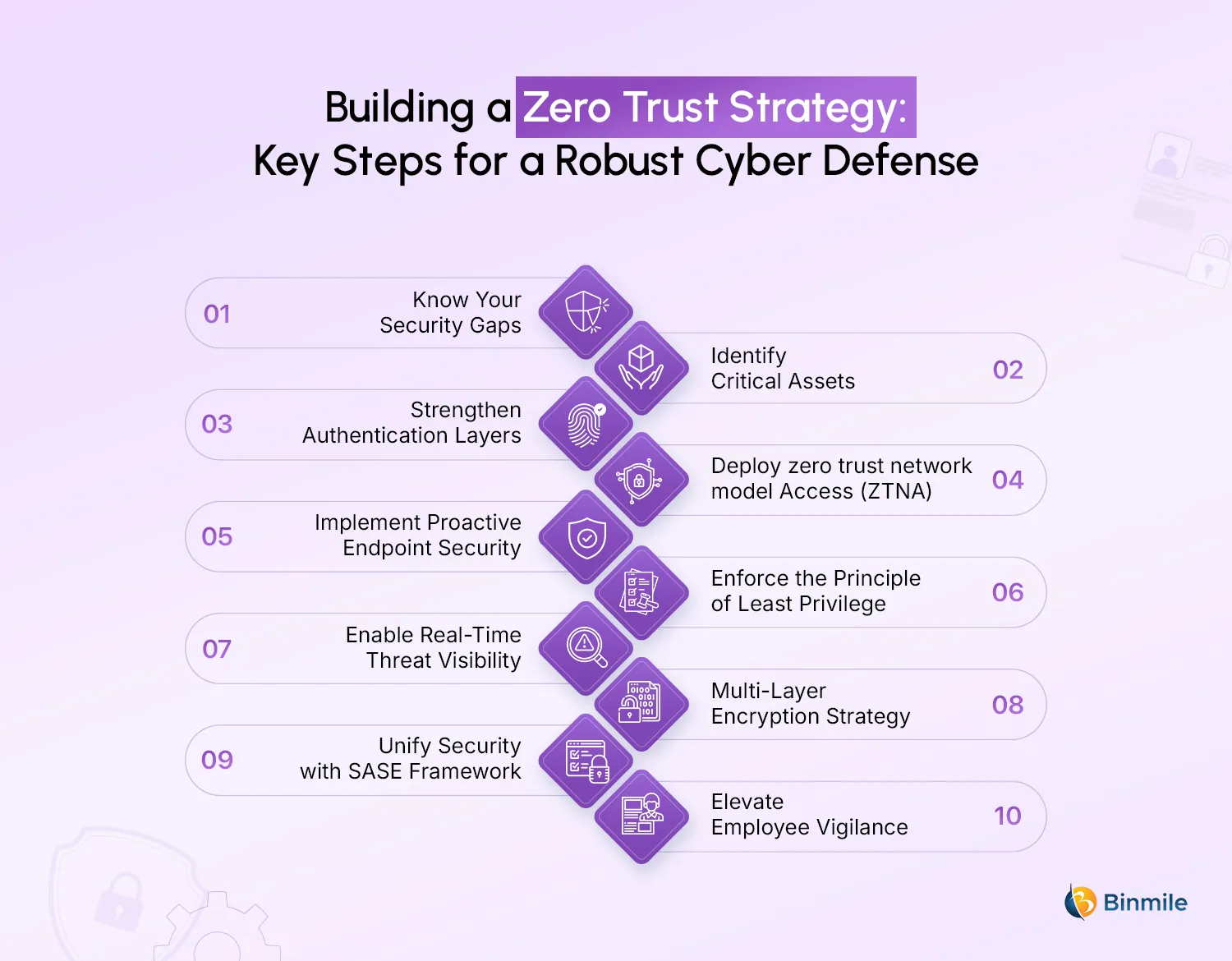
Step 1: Know Your Security Gaps
Start by auditing your existing IT environment: networks, applications, endpoints, and user access levels. Map out how data flows across systems and identify where potential risks lie, including emerging threats like gen AI security risk, which can exploit gaps in visibility and outdated tools. Look for obsolete tools, redundant permissions, and gaps in visibility. This baseline assessment helps prioritize what needs protection first and ensures your zero trust network model is grounded in your organization’s actual risk profile rather than guesswork.
Step 2: Identify Critical Assets
Instead of trying to secure everything, zero trust works best when you focus on what truly matters. Identify your “protected surface,” which includes the critical data, applications, systems, and users that directly impact business continuity. By narrowing the scope, you make security policies more precise and reduce operational overhead while keeping your most valuable assets tightly controlled from the start.
Step 3: Strengthen Authentication Layers
In a zero trust network model, identity is the new perimeter. Every user, device, and application requesting access must be verified continuously. Implement multi-factor authentication (MFA), role-based access controls, and adaptive authentication policies that adjust based on context. This ensures employees, partners, and third parties get only the access they need, nothing more, significantly reducing risks caused by compromised credentials.
Step 4: Deploy zero trust network model Access (ZTNA)
ZTNA replaces traditional VPNs by granting users access only to the specific apps and services they’re authorized to use. Instead of exposing your entire network, it creates secure, identity-driven connections grounded in secure design principles, minimizing exposure and enforcing least privilege by design. This approach not only limits attack surfaces but also improves user experience, especially for remote and hybrid teams, without compromising performance or security.
Step 5: Implement Proactive Endpoint Security
Zero Trust doesn’t just focus on networks and identities; devices matter too. Enforce strict compliance policies for any device attempting to connect, whether corporate-owned or personal. Monitor device health continuously, block non-compliant endpoints, and integrate advanced endpoint detection and response (EDR) tools. The goal is to minimize risks from compromised or unpatched devices before they become entry points for attackers.
Step 6: Enforce the Principle of Least Privilege
As one of the latest cybersecurity best practices, least privilege maintains that a user or entity should only have access to the specific data, resources, and applications needed to complete a required task. Enforce granular, context-based policies that restrict access only as necessary and prevent lateral movement within the network. Pair this with micro-segmentation, where resources are isolated into smaller, controlled zones, so even if one area is compromised, attackers can’t move freely across systems.
Step 7: Enable Real-Time Threat Visibility
A zero-trust network model demands real-time visibility. Deploy monitoring systems that track access patterns, analyze network behavior, and flag unusual activity instantly. Combine this with security information and event management (SIEM) and automated threat detection to identify potential breaches before they escalate. Continuous monitoring ensures that every request is evaluated, not just at login but throughout the session, and your business, if dealing in retail, stays protected against emerging e-commerce security threats.
Step 8: Multi-Layer Encryption Strategy
Encryption must extend beyond storage and should protect data at rest, in transit, and use. Therefore, implement strong encryption protocols and maintain strict control over key management. This ensures that even if attackers gain access to systems, the data they intercept remains unreadable. Integrating encryption into every layer of your zero trust network model builds resilience against evolving threats.
Step 9: Unify Security with SASE Framework
For distributed enterprises, Secure Access Service Edge (SASE) complements Zero Trust by combining network security and cloud-native access into one architecture. SASE integrates ZTNA, firewalls, cloud access controls, and data loss prevention, delivering secure, high-performance connections for remote and hybrid users, even during zero downtime deployments, where uninterrupted access is critical. Pairing Zero Trust with SASE ensures unified policies and visibility across on-premises and cloud environments.
Step 10: Elevate Employee Vigilance
Even the most advanced Zero Trust framework can fail without employee participation. Run regular training programs to educate staff on evolving threats, secure access practices, and their responsibilities in protecting sensitive data. Conduct phishing simulations, enforce secure password policies, and encourage a security-first mindset. A well-informed workforce creates a stronger first line of defense and helps sustain Zero Trust in the long run.
Zero Trust Network: Implementation Challenges & Fixes Explained
After understanding the tips on how to implement zero trust in your business systems and applications, let’s focus on knowing the most common obstacles you may encounter.
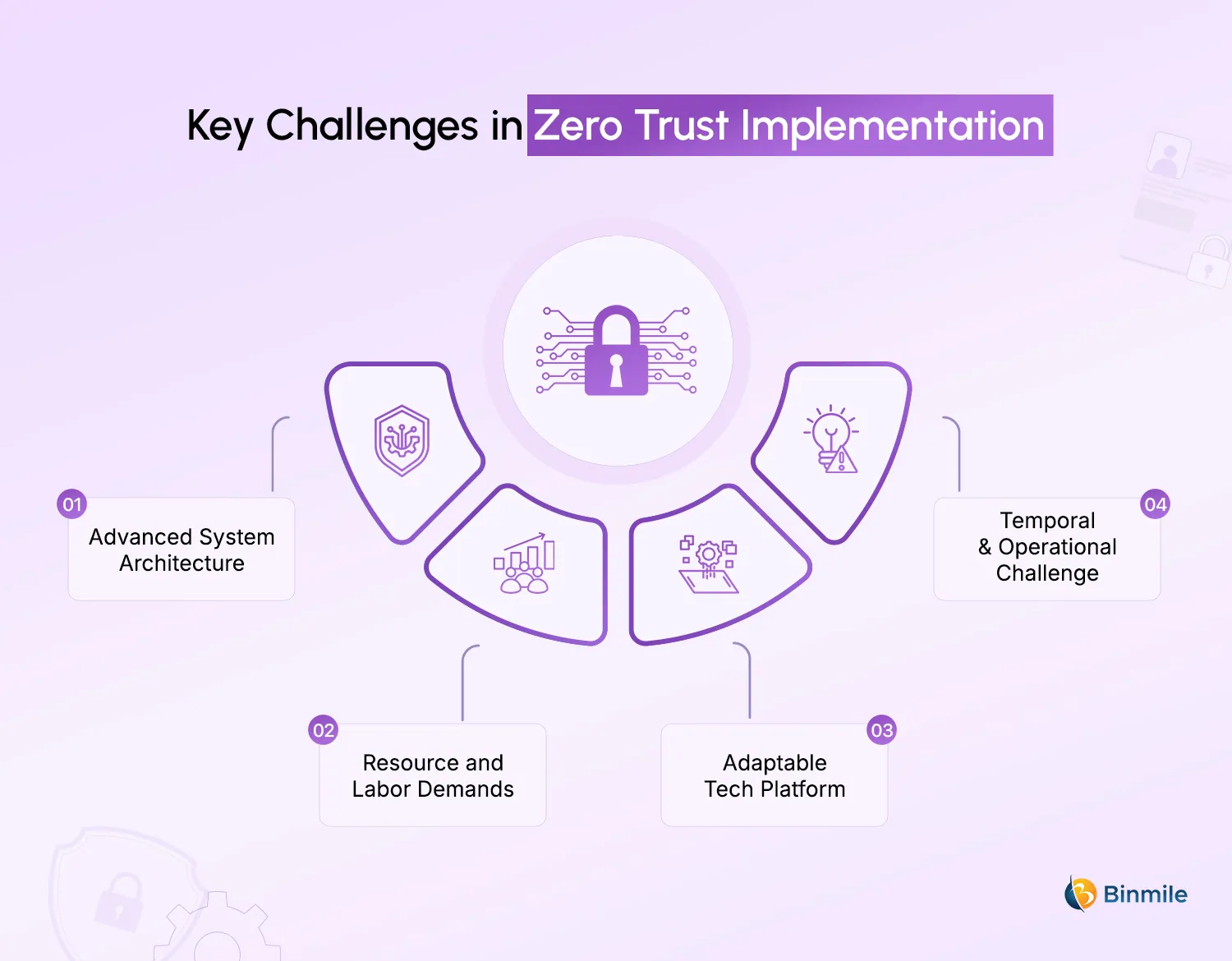
1: Advanced System Architecture
An organization’s infrastructure consists of many assets, including servers, proxies, databases, internal software development, and Software-as-a-Service (SaaS) solutions. Some of these may be running in the cloud, while others are on-premises. Therefore, it is crucial to secure each segment of your network, as well as to meet the needs of a cloud or on-premises environment, which can raise a number of obstacles. Additionally, you may have to secure a mix of legacy and new hardware and applications.
All these complications make it challenging to achieve full zero trust implementation. However, by using unified security frameworks and cloud-native controls, and expert cloud consulting services, organizations can enforce policies consistently across hybrid and legacy environments.
2: Resource and Labor Demands
It is also a resource-intensive (time, human, and financial resources) task to implement zero trust. When you need to assess who should be allowed access to which areas, it requires careful thought and collaboration. Additionally, you must spend time and effort in determining the best methods to verify the legitimacy of each user and device before granting access.
All these efforts demand hiring or allocating human resources to get this done efficiently, especially in a scenario where you do not have a system that integrates well with your environment. So, start with high-impact areas and automate identity and access management to reduce manual overhead and staffing strain.
3: Adaptable Tech Platform
This is often an overlooked element in how to implement a zero-trust model, which is the flexibility of the software to run the system. If you do not have flexible software, you may end up with redundant systems to protect all elements of your IT ecosystems.
It requires you to incorporate several micro-segmentation tools, identity-aware proxies, and software-defined perimeter (SDP) tools, which can be taxing. To avoid this, select modular platforms with open APIs to avoid tool sprawl and ensure seamless integration across your security stack.
4: Temporal and Operational Challenge
Zero Trust requires continuous oversight, and not just initial setup. Over time, access policies can become outdated, exceptions pile up, and enforcement weakens. Without regular policy reviews and transparent accountability, trust decisions lose precision and drift from actual risk conditions.
This erosion creates blind spots and undermines the core principle of “never trust, always verify.” Regular policy reviews and automated trust evaluations backed by observability for resilient systems, keeping decisions aligned with real-time risk and exposing drift before it becomes a vulnerability.
Closing Remarks on Zero Trust Implementation
We’ve explored the structured approach required for successful Zero Trust implementation, and discussed how Zero Trust is more than just a security model. It’s a strategic framework designed to safeguard data, users, and systems by removing implicit trust and enforcing verification at every step. At the same time, we highlighted the challenges organizations often face. Addressing these challenges requires a clear roadmap, stronger identity governance, and adaptive controls aligned with business needs.
If you want to transform Zero Trust from a technical concept into a scalable security strategy, consider working with data engineering experts in enterprises who operationalize Zero Trust with cloud-native architectures, automated policy enforcement, and seamless identity integration. From designing the architecture to integrating analytics and automation, they can help you strengthen your security posture and protect critical assets without disrupting operations.
Ready to build a Zero Trust foundation that secures your business today and prepares it for the threats of tomorrow? Get in touch with us and start your Zero Trust implementation journey now.